In today’s data-driven world, organizations are increasingly leveraging data analytics strategy to gain a competitive edge, understand customer behavior, and optimize operations. However, this reliance on data comes with a profound responsibility: ensuring the privacy and ethical treatment of personal information.
As regulations like GDPR and CCPA become more stringent and consumer awareness grows, a “privacy-first” approach to data analytics is no longer optional but a strategic imperative. This guide will walk you through building a robust privacy-first data analytics strategy, transforming a potential challenge into a cornerstone of trust and sustainable growth.
What is a Privacy-First Data Analytics Strategy?
A data analytics strategy is a comprehensive plan outlining how an organization collects, manages, analyzes, and uses data to achieve specific business objectives and drive informed decision-making. A privacy-first data analytics strategy takes this further by embedding data protection and ethical considerations into every stage of the analytics lifecycle. It prioritizes consent, anonymization, data minimization, and transparency, ensuring that insights are derived responsibly. This proactive stance builds customer trust, supports regulatory compliance, and can lead to improved data quality and more sustainable data use.
The shift is clear: we go from asking “what can we do with data,” to “what should we do with data, ethically and securely”?
Foundational Pillars: Key Privacy Concepts
Before building your strategy, understanding core privacy frameworks is essential.
Core Privacy Regulations: GDPR & CCPA
The General Data Protection Regulation (GDPR) in Europe and the California Consumer Privacy Act (CCPA) are landmark regulations shaping global data privacy.
- GDPR is built on principles like lawfulness, fairness, transparency, purpose limitation, data minimization, accuracy, storage limitation, integrity and confidentiality, and accountability. It grants individuals significant rights over their data, including access, rectification, and erasure.
- CCPA (as amended by CPRA) gives Californian consumers the right to know, delete, and opt-out of the sale of their personal information.
Both frameworks emphasize transparency, individual control, and organizational accountability, providing a blueprint for ethical data handling.
Privacy by Design (PbD)
Developed by Dr. Ann Cavoukian, Privacy by Design (PbD) advocates for integrating privacy into the design and operation of IT systems and business practices from the outset. Its seven foundational principles are:
- Proactive not Reactive—Preventative not Remedial: Anticipate and prevent privacy issues.
- Privacy as the Default Setting: Personal data is automatically protected.
- Privacy Embedded into Design: Privacy is a core component, not an add-on.
- Full Functionality—Positive-Sum, not Zero-Sum: Achieve both privacy and functionality.
- End-to-End Security—Full Lifecycle Protection: Secure data from collection to destruction.
- Visibility and Transparency—Keep it Open: Ensure practices are verifiable.
- Respect for User Privacy—Keep it User-Centric: Prioritize individual interests.
Integrating PbD means that systems are engineered to be both highly functional and inherently private.
Building Your Privacy-First Analytics Strategy: A Step-by-Step Guide
A privacy-first analytics strategy requires a systematic approach, integrating privacy at every phase.
Phase 1: Define Privacy-Centric Objectives & Scope
Align analytics ambitions with business goals, embedding privacy from the start. Objectives should explicitly include privacy compliance and ethical data use. Involve key stakeholders, including legal, compliance, IT, business units, and privacy experts like Data Protection Officers (DPOs). Conduct Privacy Impact Assessments (PIAs) early to identify and mitigate risks.
Phase 2: Establish Robust Data Governance for Privacy
Data governance provides the framework for managing data responsibly. This is where the “five pillars of data analytics,” adapted for privacy, come into play, drawing from information assurance principles:
- Confidentiality: Ensure information is not disclosed to unauthorized individuals or systems. Implement strong encryption and access controls.
- Integrity: Maintain the accuracy and completeness of data. Prevent unauthorized alteration or destruction.
- Availability: Ensure authorized users have timely and reliable access to (privacy-compliant) data and insights.
- Authenticity: Confirm data is genuine and from a legitimate source.
- Non-Repudiation: Provide proof of data origin and integrity, preventing denial of data processing actions.
Key governance practices include data classification by sensitivity, enforcing the principle of least privilege, rigorous data minimization (collecting only necessary data), and purpose limitation (using data only for specified, legitimate purposes).
Phase 3: Cultivate a Privacy-Aware Team & Culture
Technical safeguards are insufficient without a privacy-conscious team and culture.
- Leadership Buy-In: Senior executives must champion the privacy-first approach.
- Clear Roles & Responsibilities: Define who is accountable for privacy-related tasks.
- Comprehensive Training: Educate all employees on privacy principles, regulations, and secure data handling.
- Data Responsibility Culture: Foster a mindset where privacy is a shared responsibility.
Phase 4: Select & Implement Privacy-Enhancing Technologies (PETs)
PETs are tools that protect personal data while enabling analysis. Key PETs include:
- Anonymization & Pseudonymization: Removing or obscuring direct identifiers.
- Differential Privacy: Adding statistical noise to datasets to protect individual records while allowing aggregate analysis.
- Federated Learning: Training AI models on decentralized data without centralizing raw data.
- Homomorphic Encryption: Performing computations directly on encrypted data.
- Synthetic Data Generation: Creating artificial data that mimics real data’s statistical properties.
- Secure Multi-Party Computation (SMPC): Allowing joint computation on private inputs without revealing them.
- Trusted Execution Environments (TEEs): Secure hardware areas for processing sensitive data.
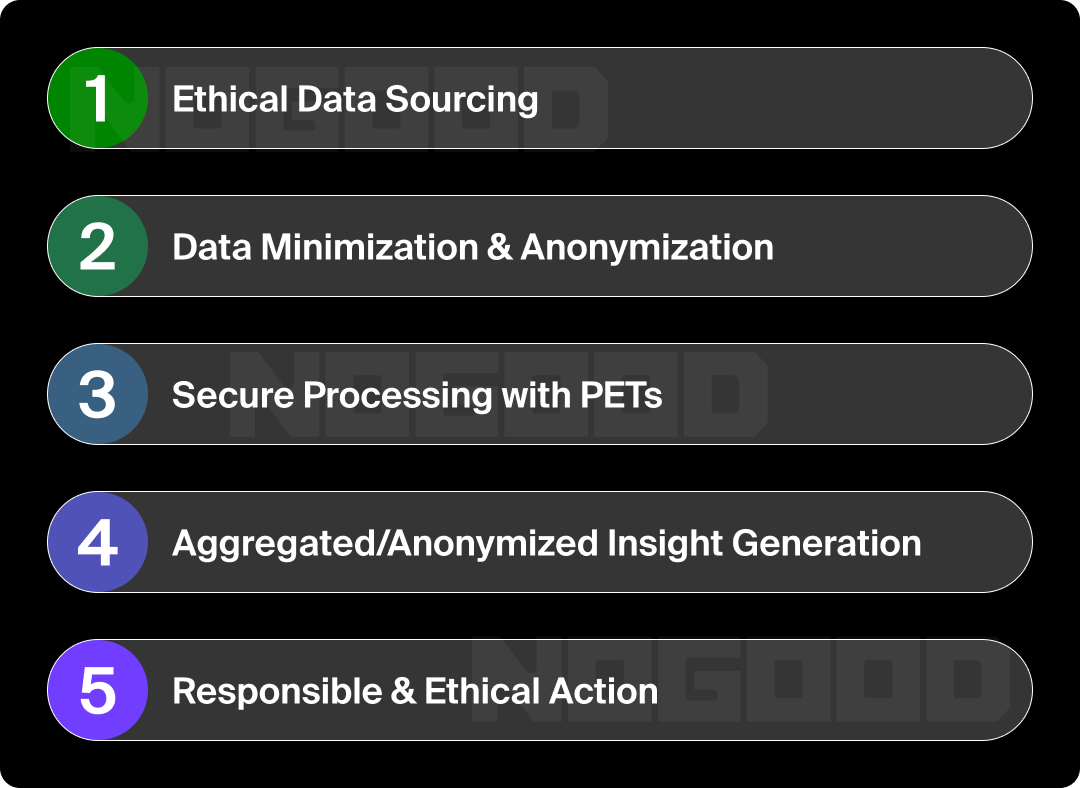
The choice of PETs should align with specific use cases, data sensitivity, and regulatory requirements. Often, a combination of PETs is most effective.
Phase 5: Ensure Ethical Data Collection, Processing & Consent
A privacy-first strategy embraces ethical data handling.
- Transparency: Clearly communicate what data is collected, why, and how it will be used.
- Consent Mechanisms: Obtain explicit, granular, and easily manageable consent where required.
- Ethical AI & Analytics: Consider societal impacts, fairness, algorithmic bias, and potential discrimination. Biased analytics can lead to unfair outcomes.
Phase 6: Performing Analytics with Privacy at the Forefront
Apply privacy-enhancing techniques during the analysis itself. The four main types of data analytics each have specific privacy considerations:
- Descriptive Analytics (What happened?): Summarizes historical data. Ensure reports do not inadvertently reveal PII, especially with granular data.
- Diagnostic Analytics (Why did it happen?): Examines past data to find root causes. Protect sensitive individual information during drill-downs or when analyzing system data.
- Predictive Analytics (What could happen?): Forecasts future outcomes. Address potential biases in models to prevent discriminatory outcomes and ensure fairness. Secure data used for training.
- Prescriptive Analytics (What should we do about it?): Recommends actions. Ensure recommendations are ethical, don’t rely on overly intrusive data, and don’t lead to unfair treatment.
Use secure data sharing and reporting mechanisms, aggregating or anonymizing insights where necessary.
Phase 7: Sustain Privacy: Monitoring, Auditing & Adapting
A privacy-first strategy is ongoing.
- Continuous Monitoring & Auditing: Regularly review data handling practices, PET effectiveness, and compliance.
- Regularly Update Policies: Adapt to new regulations, technologies, and societal expectations.
- Incident Response Plan: Prepare for data breaches with clear procedures for containment, investigation, notification, and remediation.
- Feedback Mechanisms: Allow individuals and internal teams to report privacy concerns.
Navigating Challenges & Embracing Best Practices
As with most things, implementing a privacy-first strategy has its challenges:
- Data Quality & Integration: Inconsistent or siloed data can undermine privacy measures and analytics.
- Solution: Strong data governance, data cleaning processes, and secure integration tools.
- Complexity & Cost of PETs: PETs can be technically demanding and resource-intensive.
- Solution: Start with foundational PETs, conduct pilot projects, and focus on long-term ROI.
- Balancing Utility & Privacy: Overly aggressive anonymization can reduce data’s analytical value.
- Solution: Nuanced selection of PETs, context-aware techniques.
- Organizational Resistance to Change: Employees may resist new processes.
- Solution: Leadership advocacy, comprehensive training, and clear communication of benefits.
- Resource Allocation: Budget, skilled personnel, and infrastructure can be hurdles.
- Solution: Strategic investment based on risk and business impact.
- Evolving Regulatory Landscape: Keeping up with changing laws is complex.
- Solution: Dedicated compliance oversight and adaptable governance frameworks.

Best practices include establishing strong governance, prioritizing data minimization, investing in training, adopting a risk-based approach, embracing transparency, and iterating continuously.
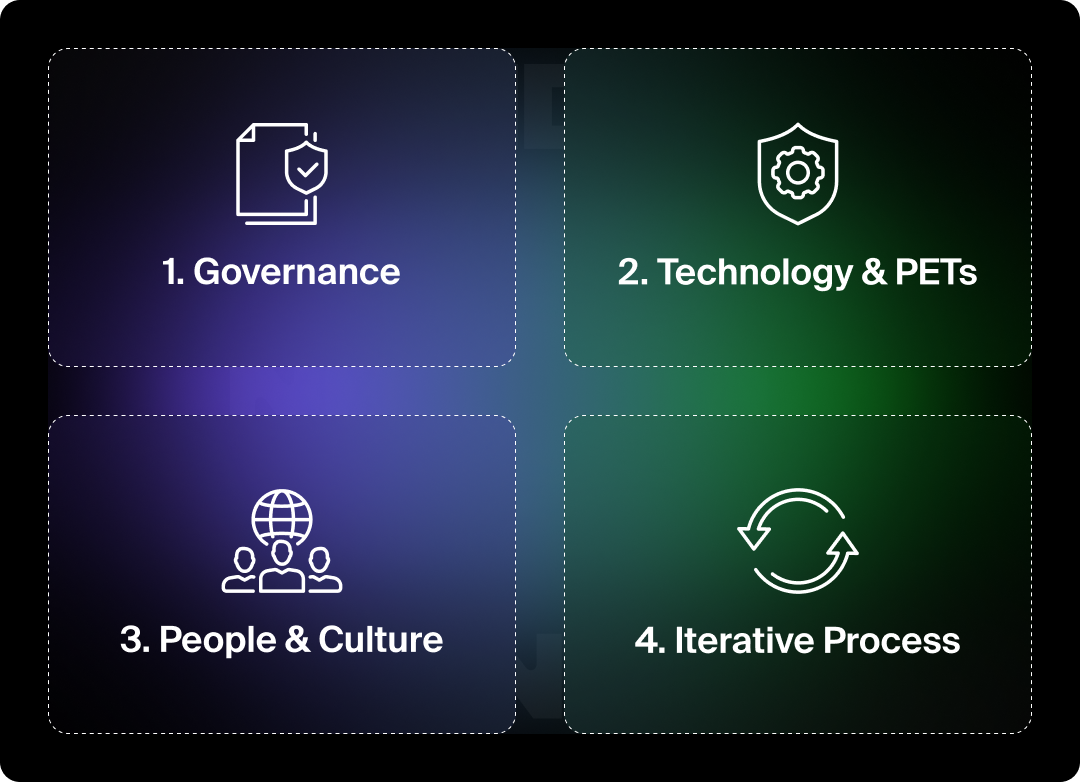
The 5 Essential Components of a Data Analytics Strategy (With a Privacy-First Focus)
While the above phases provide a roadmap, a successful privacy-first data strategy fundamentally relies on five interconnected components:
- Alignment with Business & Privacy Objectives: Ensure data initiatives and privacy goals support overarching business aims.
- Privacy-Aware Data Architecture & Technology: Design systems and select tools (including PETs) that inherently support privacy from the ground up.
- Empowered People & Privacy-Centric Culture: Cultivate a skilled team and an organizational culture that understands, values, and prioritizes data privacy.
- Robust Data Governance & Embedded Compliance: Implement strong policies, clear roles, and processes for ethical, legal, and secure data handling, embedding Privacy by Design.
- Clear Roadmap & Iterative Improvement with Privacy Milestones: Develop an evolving plan with specific privacy objectives, metrics, and a commitment to continuous refinement.
The Future is Privacy-First—Embrace Privacy as a Catalyst for Innovation & Growth
The journey towards a privacy-first analytics strategy is an investment in your organization’s future. In an era defined by data abundance and heightened privacy consciousness, the ability to analyze information responsibly is no longer a niche concern but a fundamental determinant of sustainable success.
Adopting a privacy-first approach is not about constraining innovation or limiting the potential of data—rather, it is about unlocking new avenues for growth, building enduring, trust-based relationships with customers, and navigating the complex regulatory landscape with confidence.
By systematically embedding privacy principles into the vision, governance, architecture, technologies, and culture surrounding data analytics, businesses can transform a potential liability into a significant asset.
The benefits are clear: enhanced brand reputation, strengthened customer loyalty, improved data quality leading to more reliable insights, assured regulatory compliance, and a distinct competitive advantage. As we move further into 2025, organizations that prioritize telling customers what data is being collected and how it’s being used, keeping it only for limited periods, and enabling data subject rights will be the ones that thrive.
Frequently Asked Questions
What is strategy in data analytics?
A strategy in data analytics is a comprehensive blueprint or well-defined plan that guides how an organization collects, stores, manages, analyzes, and utilizes data to achieve specific business goals and drive innovation. It establishes the necessary processes, policies, technologies, and defines the roles of people involved in the data lifecycle, ensuring alignment between data activities and overarching business objectives.
What are the 4 main types of data analytics?
- Descriptive Analytics: Focuses on summarizing historical data to understand what happened?
- Diagnostic Analytics: Examines data to understand the root causes of past outcomes, answering why did it happen?
- Predictive Analytics: Uses historical data, statistical models, and machine learning to forecast what will happen in the future?
- Prescriptive Analytics: Recommends specific actions to achieve desired outcomes or optimize decisions, addressing what should we do about it?
What are the 5 pillars of data analytics?
- Privacy-Aware Data Collection: Gathering relevant, high-quality data with explicit consent and transparency, focusing on data minimization.
- Secure & Compliant Data Storage: Securely archiving and managing data, adhering to retention policies and privacy regulations.
- Ethical Data Preparation & Cleaning: Transforming and cleaning data to ensure accuracy and usability, without introducing bias or compromising privacy.
- Purpose-Driven & Fair Data Analysis: Applying appropriate analytical techniques for defined purposes, ensuring fairness and avoiding discriminatory outcomes.
- Transparent Data Visualization & Communication: Presenting insights in an understandable and transparent manner, clearly communicating how data was used and any limitations.
What are the 5 essential components of a data strategy?
- Privacy-Infused Vision, Objectives & Roadmap: Aligning data and analytics capabilities with business strategy, with privacy as a core objective, and including a realistic implementation roadmap.
- Privacy-Centric Data Governance: Defining organizational accountability, controls, and decision-making processes for data standards, quality, compliance, and critically, privacy.
- Privacy-Enabling Data Architecture & Technology: Designing systems and choosing tools that incorporate “Privacy by Design” and leverage PETs.
- Privacy-Aware People & Culture: Building the right team and skills, and fostering a data-literate culture that also prioritizes and understands data privacy responsibilities.
- Secure & Ethical Information Operations & Management: Defining how data is created, maintained, updated, archived, and deleted, ensuring data trustworthiness, quality, and ethical handling throughout its lifecycle.